How to Set Up DMARC Forensic Report Encryption with PGP

We will go over how to set up DMARC forensic report encryption with PGP in this article.
As DMARC forensic reports contain Personally Identifiable Information (PII), we recommend that you encrypt such reports, so that only those who have the permission can access them.
DMARCLY uses Pretty Good Privacy (PGP) to encrypt DMARC forensic reports. Once set up, DMARCLY uses the public key to encrypt incoming DMARC forensic reports and save them in the database. You can download an encrypted report in the dashboard, submit it to a PGP decryption tool, along with your priviate key and passphrase, and get back the decrypted report.
On a high level, this involves a few steps: create a PGP key pair, upload the public key to DMARCLY, and decrypt encrypted reports with your private key.
Step 1. Create a PGP key pair
Various free tools exist to allow you to create a PGP key pair. One of these is the gpg (GNU Privacy Guard, aka GPG) tool on Ubuntu. It offers useful commands to create, list, export key pairs, and much more.
To learn how to install and use gpg on Ubuntu, refer to this post.
Specifically, the following are the commands for the tasks required for this step:
To create a key pair:
gpg --gen-keyBe sure to keep the passphrase in a safe place, as it's required for decrypting reports later.
To export a public key:
gpg --output ~/public.key --armor --export your_email@address.comStep 2. Upload public key to DMARCLY
Let's say you have successfully created a key pair and exported the public key as public.key, now you need to upload it to DMARCLY to enable encryption for forensic reports.
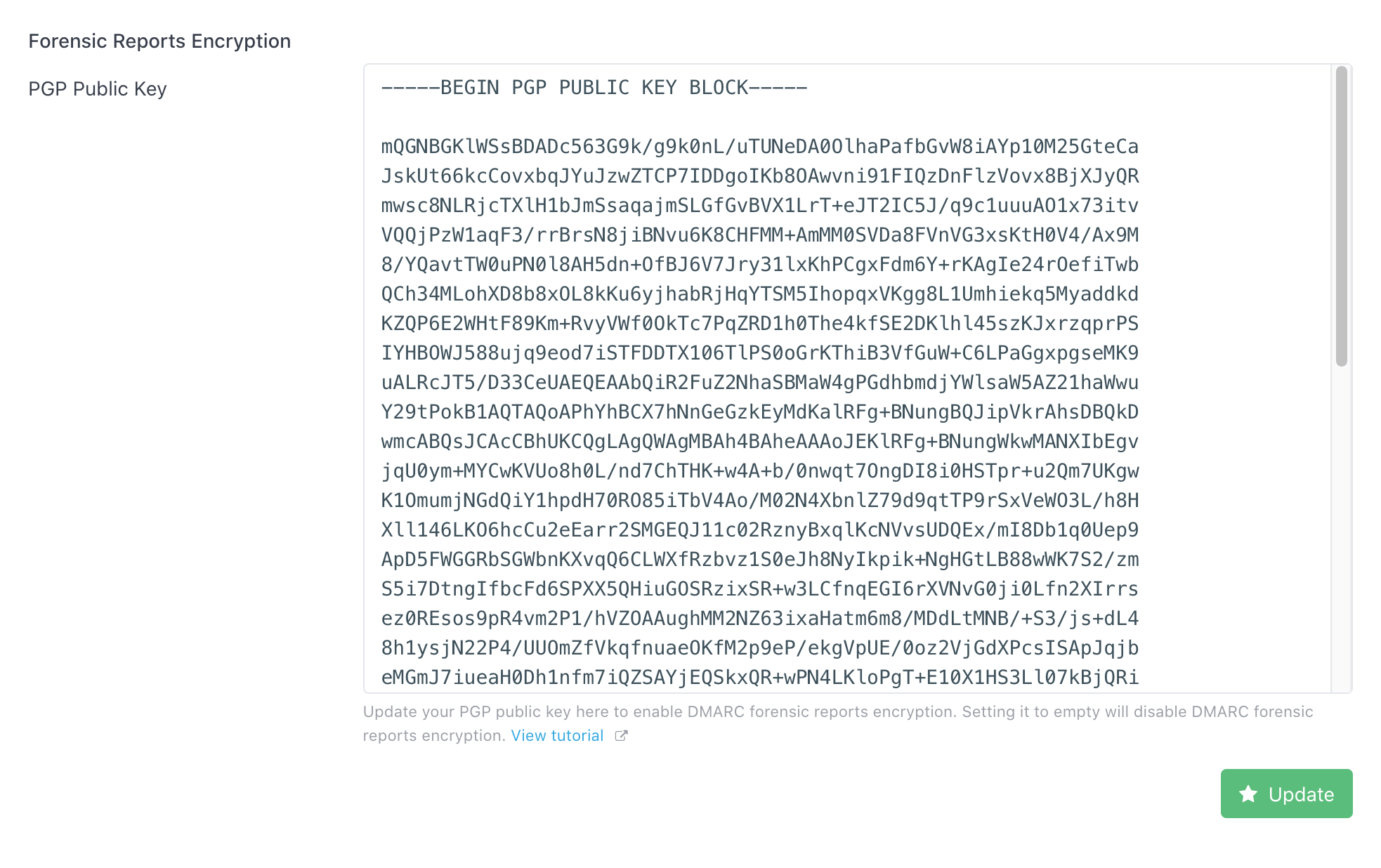
Open the file public.key with any text editor, copy all the content, then log in to the DMARCLY dashboard, go to System, paste it in the PGP Public Key field in the Forensic Report Encryption section, then click the Update button.
It should look similar to the following:
Step 3. Decrypt encrypted reports with private key
Once you find any encrypted forensic report in the dashboard, you can decrypt it with your private key and passphrase. You need to use the gpg command export-secret-keys for this purpose.
To export a private key:
gpg --export-secret-keys --armor XXXXXXXX > ./my-priv-gpg-key.ascRemember to replace XXXXXXXX with your hexadecimal key ID.
Next open an encrypted forensic report in the dashboard, click the Copy Encrypted Forensic Feport to Clipboard button to copy the complete report, as shown below:
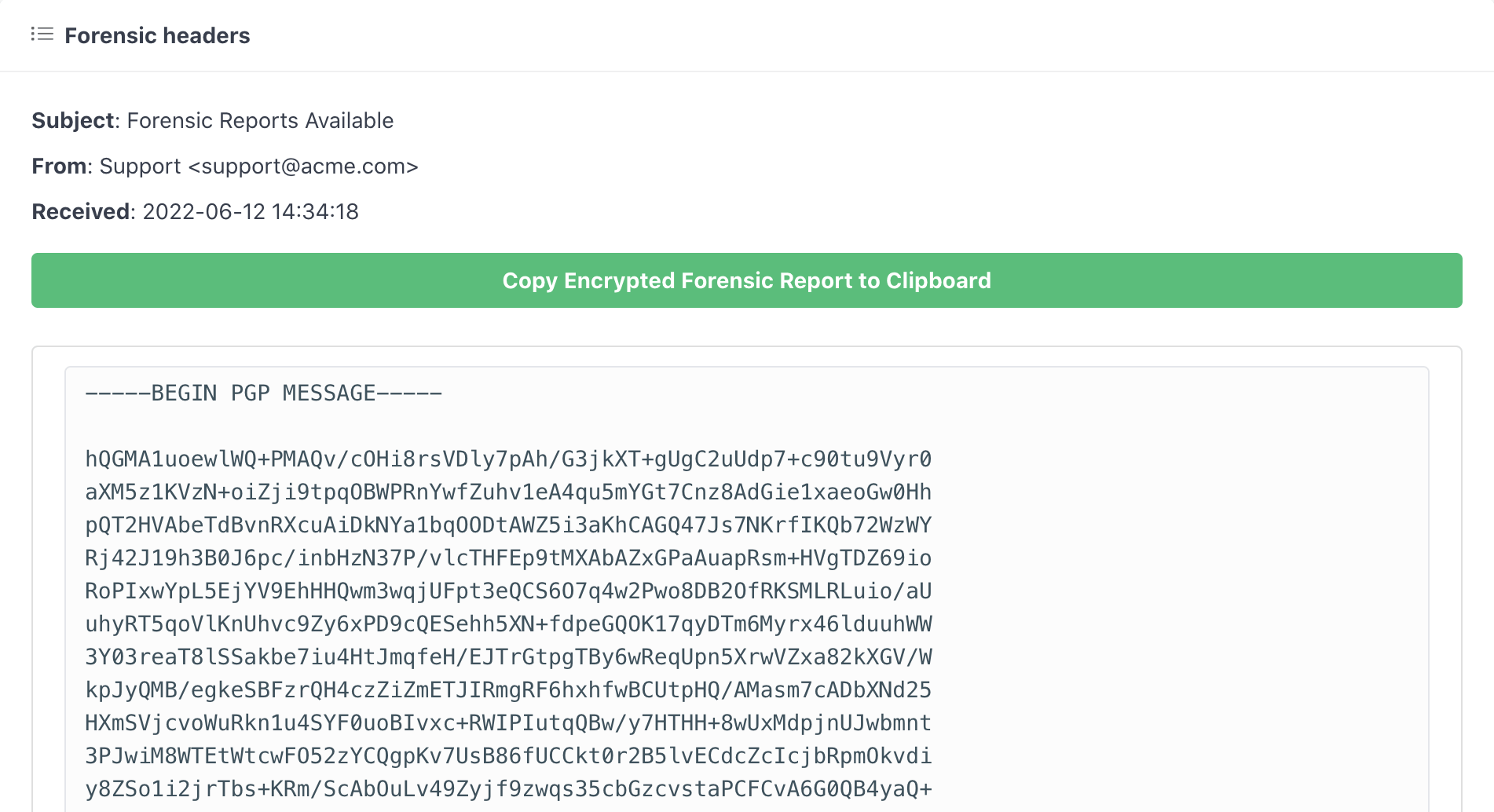
Now that you have the encrypted report, private key, and passphrase, it's time to submit them to a decryption tool to get the original report. You can use https://8gwifi.org/pgpencdec.jsp to decrypt it online without having to install any software.
You must use the private key that matches the public key uploaded in our dashboard to decrypt a forensic report.
Предыдущая запись Следующая запись
Protect Business Email & Improve Email Deliverability
Get a 14 day trial. No credit card required.
Create Account