What is DMARC Identifier Alignment (domain alignment)?

Email end users check the from field in their email clients to tell where an email comes from. However, SPF doesn't authenticate the field, neither does DKIM. This means "what you see might not be what's been authenticated". That's why the identifier alignment mechanism is introduced in DMARC.
Security hole in SPF
There are two from addresses in email: the envelope from address that is specified by the mail from command in an SMTP session, while the header from address is the address specified in the From header field in the SMTP data command.
By design, SPF only authenticates the envelope from address, leaving the header from address unchecked. This means that spoofers can still send the end user an email from one of the servers on the whitelist with a spoofed header from address. In other words, the from field the email end users sees in his/her email client might be different from what's been authenticated by SPF.
Security hole in DKIM
Similarly, DKIM only authenticates the d= value in the DKIM-signature, which can be different from the domain value in the header from address. The indication is obvious: the from field the email end users sees in his/her email client might be different from what's been authenticated by DKIM.
What is the central identity, and why?
The role of the central identity of an email is to identify the originator of the email for the end user. DMARC picks the domain in the header from address as the central identity for two reasons:
- the header from address is what the end user perceives as the originator of the email;
- the header from address is guaranteed to exist.
The idea is to associate what the email end user perceives as with something that's validated by SPF and DKIM. That is, "what you see is what's been validated/authenticated". Loopholes in SPF/DKIM patched!
Organizational Domains
The organizational domain is the "root part" of a domain. For instance, the organizational domain of mail.domain.com is domain.com.
Organizational domain is used to check identifier alignment in relaxed mode of DMARC.
What is DMARC identifier alignment?
DMARC identifier alignment, also known as DMARC alignment/domain alignment, is a mechanism introduced in DMARC to ensure at least one of the domains authenticated by SPF or DKIM to "align with" the domain found in the from header address - the central identity. Identifier alignment is sometimes called domain alignment.
DMARC has two alignment modes: strict and relaxed. In the strict alignment mode, two domains must be identical in order for them to align with each other; in the relaxed alignment mode though, two domains align when their organizational domains are identical.
Identifier alignment in SPF
In SPF, identifier alignment means the domain portion of the envelope from address aligns with the domain found in the header from address. If the envelope from address is empty, alignment is checked against the EHLO domain.
Here are a few examples.
Example A: SPF in alignment
Envelope from address
<john@business.com>Header
From: john@business.com
Date: Fri, Feb 25 2019 03:14:20 -1200
To: jane@example.org
Subject: Hi!The envelope from address and the header from address have identical domains. Therefore, they are aligned.
Example B: SPF in alignment (organizational domain)
Envelope from address
<john@mail.business.com>Header
From: john@business.com
Date: Fri, Feb 17 2019 15:14:10 -1200
To: jane@example.org
Subject: Hello!The envelope from domain is a subdomain of the header from domain. Thus, the identifiers are in alignment if relaxed SPF mode is applied, and not in alignment if strict SPF mode is applied.
Example C: SPF not in alignment
Envelope from address
<john@business.com>Header
From: john@business.org
Date: Fri, Feb 15 2019 13:14:20 -1200
To: jane@example.org
Subject: Hello!The envelope from address and the header from address are neither the same nor share the same organizational domain. Thus, the identifiers are not aligned.
SPF authenticated VS SPF aligned
What is the difference between SPF authenticated and SPF aligned?
If an email message came from an IP address specified on the IP address list in the SPF record, the message was SPF authenticated.
On the other hand, if an email message:
- was SPF authenticated; AND
- had DMARC identifier alignment in SPF
it was SPF aligned.
If an email stream passed SPF (SPF Authenticated: pass) but was SPF unaligned (SPF Aligned: fail), it meant that the emails came from an IP address specified in the SPF record, but did not have DMARC identifier alignment.
The following is an example of an email stream on acmecorp.com that was SPF authenticated (SPF Authenticated: pass), but not SPF aligned (SPF Aligned: fail):
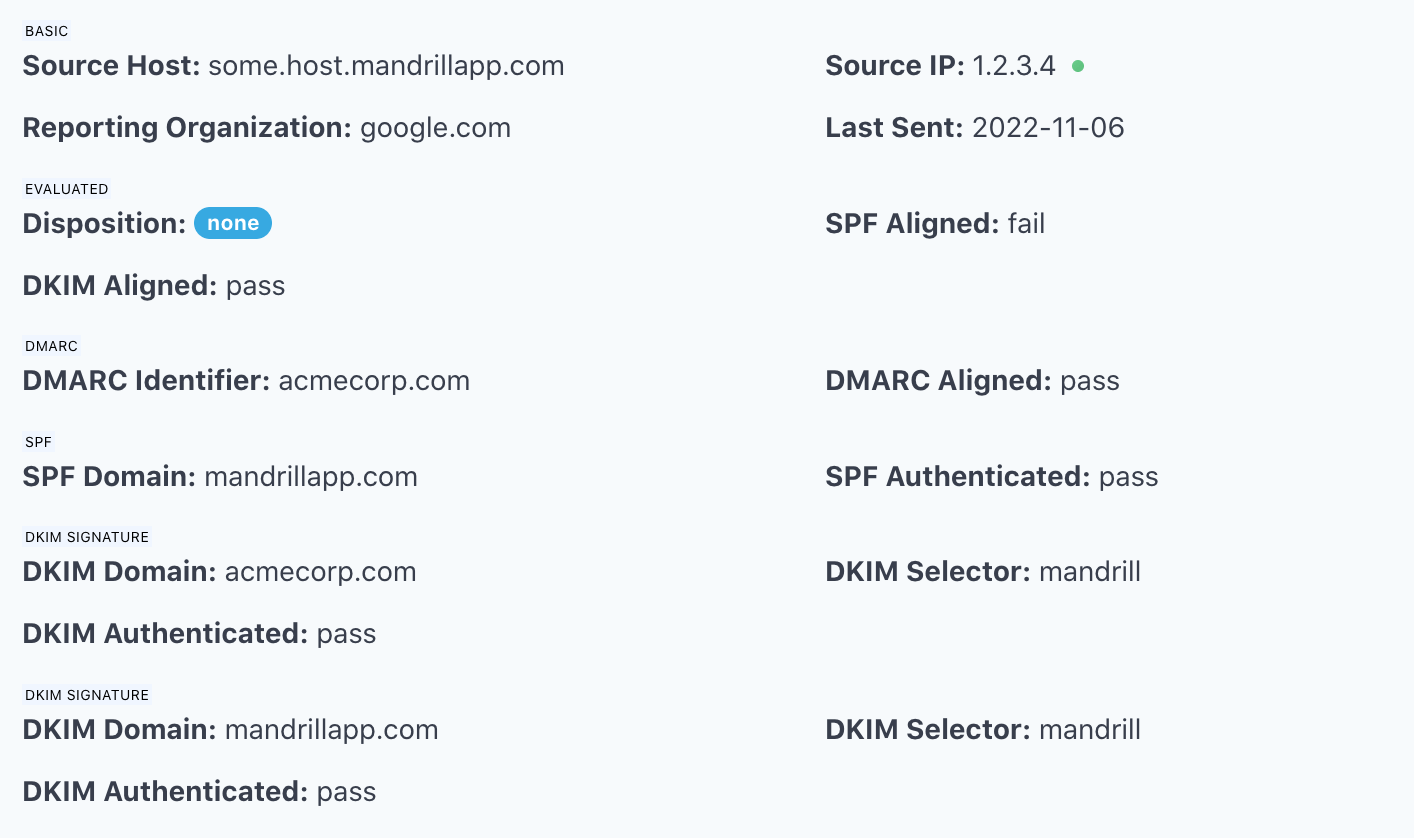
In this example, the SPF record on acmecorp.com includes mandrillapp.com, and the message came from one of mandrillapp.com's hosts (Source Host: some.host.mandrillapp.com). Therefore, SPF Authenticated was pass.
However, because SPF Domain was mandrillapp.com while DMARC Identifier was acmecorp.com, there was no identifier alignment in SPF. Therefore, SPF Aligned was fail.
Identifier alignment in DKIM
In DKIM, identifier alignment means that the domain value in the d= field of DKIM-signature in the email header has to align with the domain found in the header from address.
Here are a few examples.
Example A: DKIM in alignment
d= domain
business.comHeader
From: john@business.com
Date: Fri, Feb 25 2019 03:14:20 -1200
To: jane@example.org
Subject: Hi!The domain in the header from address is the same as the d= domain. Therefore, they are aligned.
Example B: DKIM in alignment (organizational domain)
d= domain
mail.business.comHeader
From: john@business.com
Date: Fri, Feb 17 2019 15:14:10 -1200
To: jane@example.org
Subject: Hello!The d= field is a subdomain of the header from domain. Thus, the identifiers are in alignment if relaxed DKIM mode is applied, and not in alignment if strict DKIM mode is applied.
Example C: DKIM not in alignment
d= domain
business.comHeader
From: john@business.org
Date: Fri, Feb 15 2019 13:14:20 -1200
To: jane@example.org
Subject: Hello!The d= field is different than the header from domain. Thus, the identifiers are not aligned.
DKIM authenticated VS DKIM aligned
What is the difference between DKIM authenticated and DKIM aligned?
If an email message was signed with a valid signature and the signature was verified on the receiving server, the message was DKIM authenticated.
On the other hand, if an email message:
- was DKIM authenticated; AND
- had DMARC identifier alignment in DKIM
it was DKIM aligned.
If an email stream passed DKIM (DKIM Authenticated: pass) but was DKIM unaligned (DKIM Aligned: fail), it meant that the emails were signed with valid DKIM signatures, but did not have DMARC identifier alignment.
The following is an example of an email stream on acmecorp.com that was DKIM authenticated (DKIM Authenticated: pass), but not DKIM aligned (DKIM Aligned: fail):
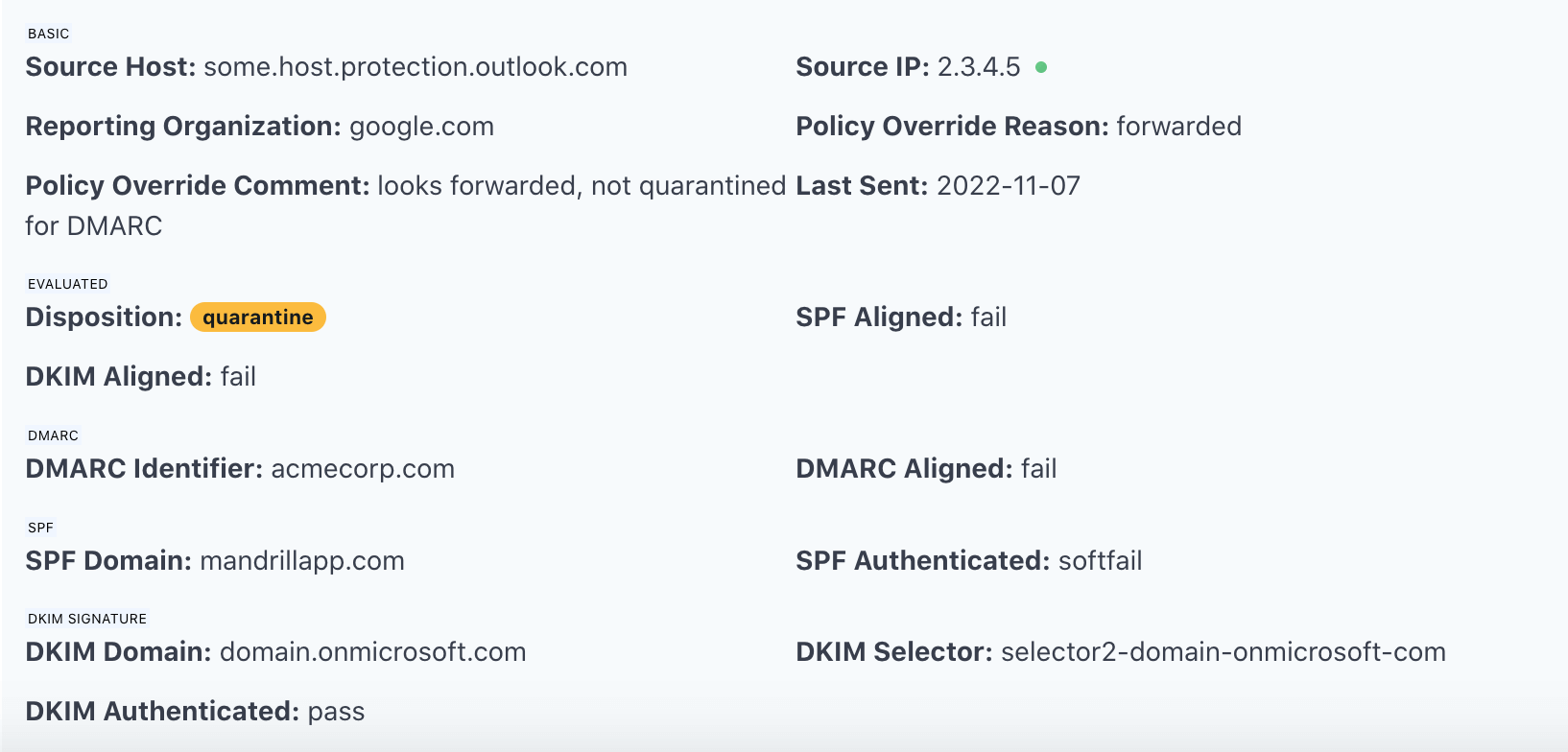
In this example, each of these messages was signed with a valid signature with a DKIM key under selector2-domain-onmicrosoft-com, and the signature was verified on the receiving server. Therefore, DKIM Authenticated was pass.
However, because DKIM Domain was domain.onmicrosoft.com while DMARC Identifier was acmecorp.com, there was no identifier alignment in DKIM. Therefore, DKIM Aligned was fail.
Article précédent Article suivant
Protect Business Email & Improve Email Deliverability
Get a 14 day trial. No credit card required.
Create Account
